ISO 27001 is the most widely used and respected information security standard in the world, released by the ISO (International Organization for Standardization). The Standard provides the foundation for an efficient Information Security Management System (ISMS). All the risk controls required for strong IT security management are included, along with a description of the policies and processes required to safeguard organizations.
The scope of ISO 27001 certification goes beyond IT. ISO 27001 prioritizes data protection online and offline. Organizations of all sizes may benefit from ISO 27001 audit. The new ISO 27001 changes need your firm to stay current to prevent cyberattacks.
By showing stakeholders, clients, and suppliers how seriously you take ISMS Certification sets your firm apart.
What is ISO 27001?
When it comes to ISMS, the most well-known standard in the world is ISO 27001. It specifies what an ISMS needs to be able to do. The ISO/IEC 27001 standard offers comprehensive guidance for organizations across all sectors and sizes regarding the establishment, implementation, maintenance, and ongoing enhancement of an information security management system.
If a company or organization meets ISO/IEC 27001, it has built a risk management system to secure its data and follows all of its best practices and principles. ISO 27001 certification indicates an entity has satisfied Clause 4.4 of the ISMS standard and shown conformity with independent ISO certification bodies and external auditors. ISO 27001 accreditation distinguishes your organization and convinces peers that you can manage sensitive third-party data and intellectual property. This opens several doors and reduces corporate risk.
Why Do You Need ISO 27001 Certification?
The escalating rate of cybercrime and the perpetual emergence of new threats can make cyber risk management challenging, if not impossible. Organizations that use an ISO/IEC 27001 system are better able to recognize risks and take proactive measures to mitigate them. The information security holistic approach—vetting of people, policy, and technology—is encouraged by ISO/IEC 27001. This standard provides a framework for managing risks, building cyber resilience, and achieving operational excellence via information security management systems.
ISO 27001 Certification shows that your company's people, processes, equipment, and systems follow a framework. Imagine a world without financial reporting or health and safety requirements. Information security lags in certification and independent audits. Since change is occurring quicker for virtually everything, creative firms are making progress inside, notably in their supply chains. There are two ways to perceive ISO 27001 certification:
-
Trust in your vendors
Customers need to be confident that their suppliers are qualified to reduce business risks and take advantage of possibilities, such as reduced overall costs and less risk associated with the job they do for you, and more consistent, higher standards.
-
Establishing credibility for your company
As customers become more savvy, knowing your supply chain is secure is crucial. Influential customers move risk management down the supply chain by requesting ISO 27001 certification. There are more benefits to ISO 27001 certification besides greater revenue. Knowledgeable workers want renowned organizations.
What are the benefits of ISO 27001 Audit?
Implementing an ISO 27001 framework has the following major benefits:
- Meet Compliance: An ISMS verifies that you follow widely recognized information security standards. This helps you meet your legal responsibilities and follow rules (for example, SOX).
- Gain Confidentiality: It ensures the protection of sensitive information by implementing strict security guidelines and access control, enabling the safe sharing of data.
- Manage Risks: Customer and stakeholder trust in your data security risk management is strengthened by the Standard's ability to manage and minimize risk exposure.
- Gain satisfaction of customers: Boosting consumer confidence and happiness via better information security measures results in better client retention.
- Build a Security Culture: With the support of their employees and other stakeholders, businesses can establish a security culture.
- Comprehensive protection: Improved security procedures and increased knowledge of security responsibilities all contribute to the company's, its assets', shareholders', and directors' protection.
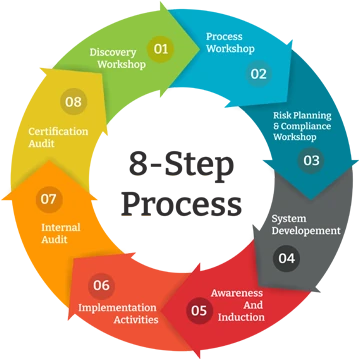
Maintaining your (ISMS) ISO 27001 Certification
A three-year cycle is used for ISO 27001 certification:
- Initial surveillance audit: (typically once a year, although depending on size, scope, and risk, it can occur more often)
- Second surveillance audit
- Re-certification after three years of certification audit.