Deep Dive into the latest OWASP API Security Top 10 2023.
In an increasingly interconnected digital landscape, Application Programming Interfaces (APIs) play a crucial role...
API Security Testing is to identify, classify and exploit potential vulnerabilities in Application Programming Interfaces (API) and Web Services. Security Assessments aids the developers to timely remediate the vulnerabilities, enhance its overall security and safeguard the software from any unauthorized access which can cause a negative impact on the organization.
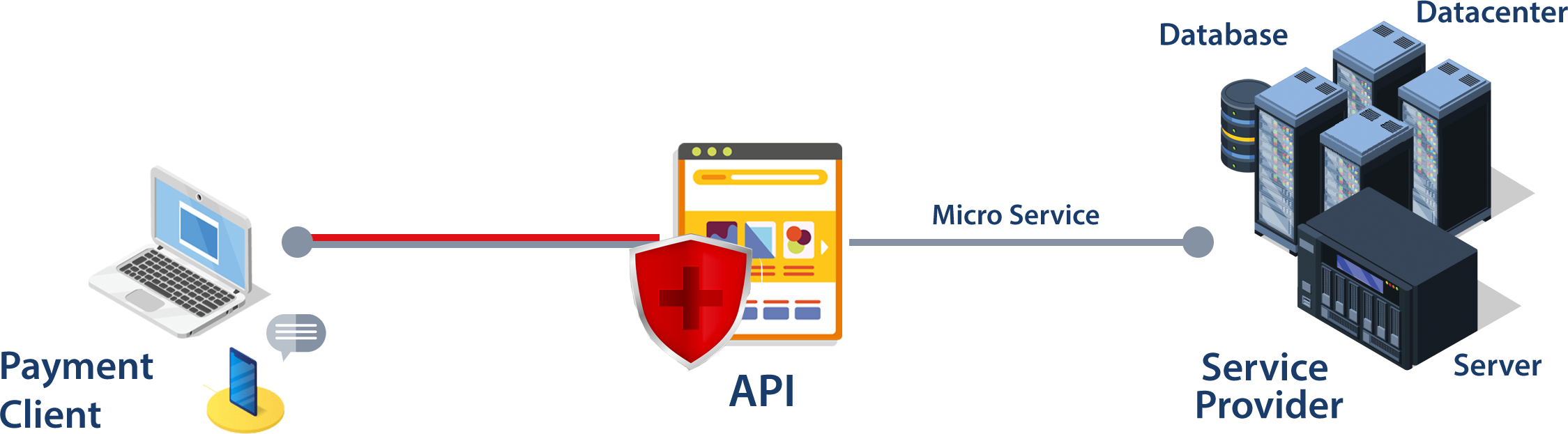
APIs expose application logic and sensitive data such as Personally Identifiable Information (PII) and hence the vulnerability. Advancements in the web technologies have increased the use of the API owing to their capability in providing ease in usage of the software technologies.
Hence assessments like API security testing as per OWASP API Top 10 2019, helps the developers to remediate vulnerabilities that may cause a potential impact on the organization or on business.